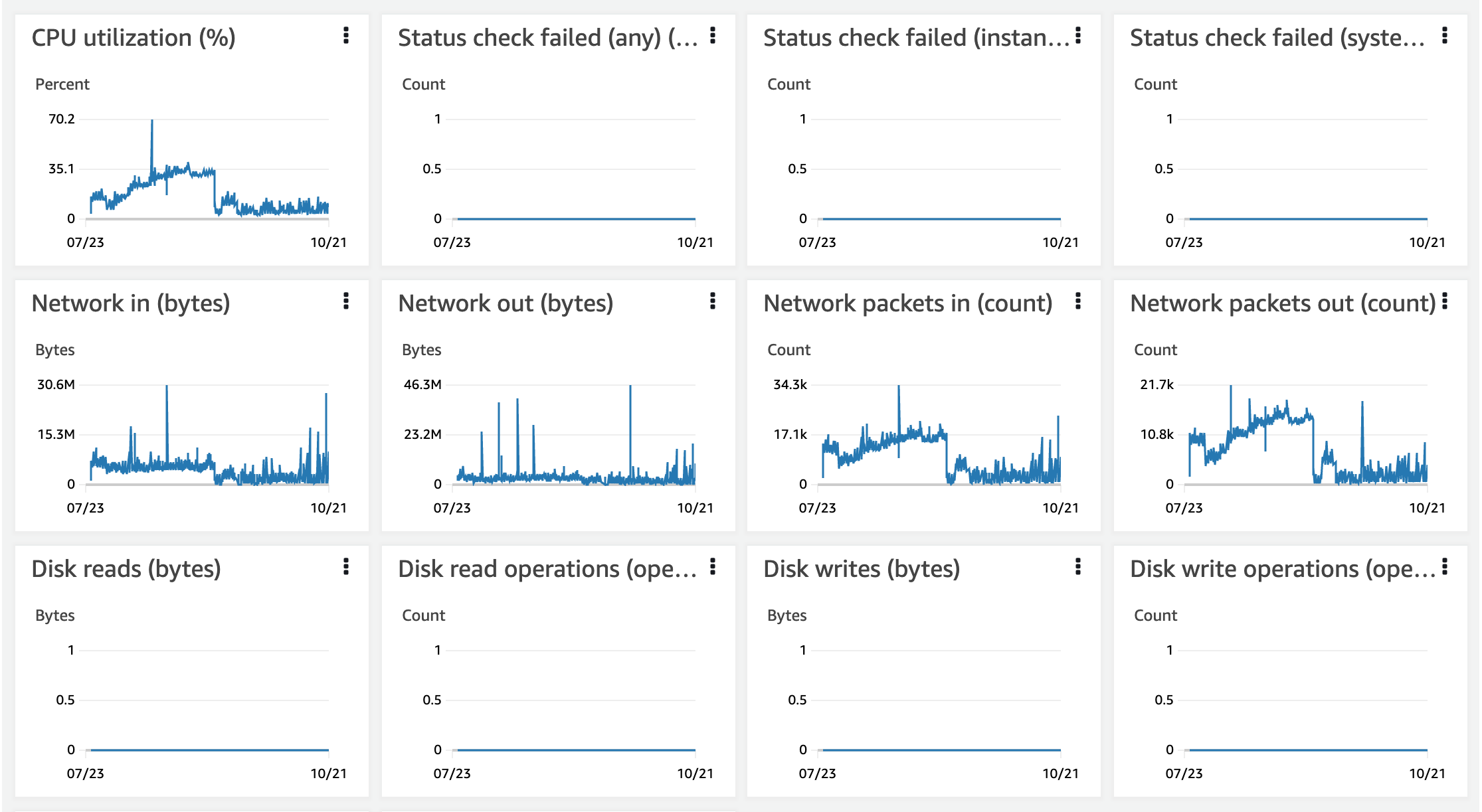
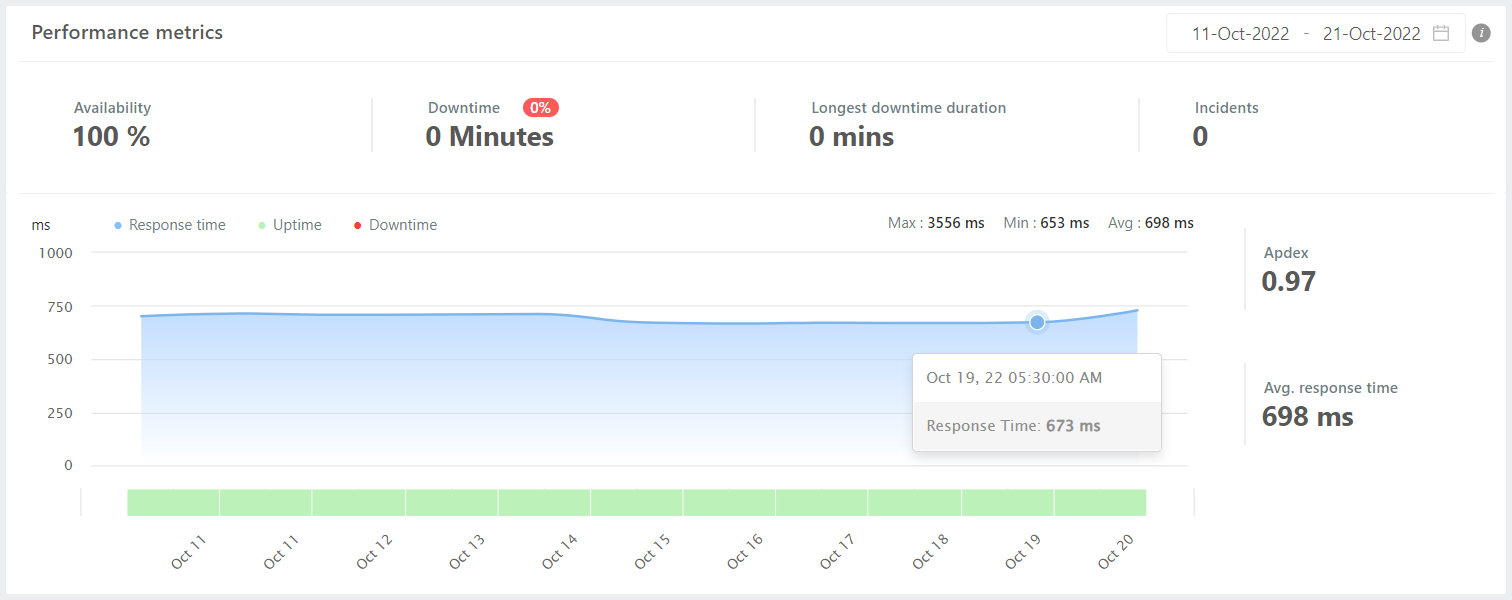
Security patches
Security patches are regularly updated on the server to ensure the latest exploits are patched at the earliest.
UFW Firewall
In addition to the AWS Network firewall, the UFW firewall is deployed on the server to again restrict access to all ports except HTTPS and SSH.
Fail2ban
A fail2ban service also continuously runs on the server that scans for multiple requests on the open SSH and HTTPS ports. This service throttles requests from the same IP and bans multiple attempts to access the same service within a certain period of time.
Freshclam Antivirus
The Freshclam antivirus continuously runs on the platform. This scans for any virus or malware that can be uploaded to the server from the frontend.
OpenSSH
OpenSSH is configured to disallow connections on the standard port 22(and use a non-standard port), restrict logins to only one user (non-root), support only protocol 2 logins and disallow any password-based logins. This prevents standard attacks on SSH.
Security Login
Logins are secured with only private-public key logins, all root logins are disabled and all standard users are removed from the server.